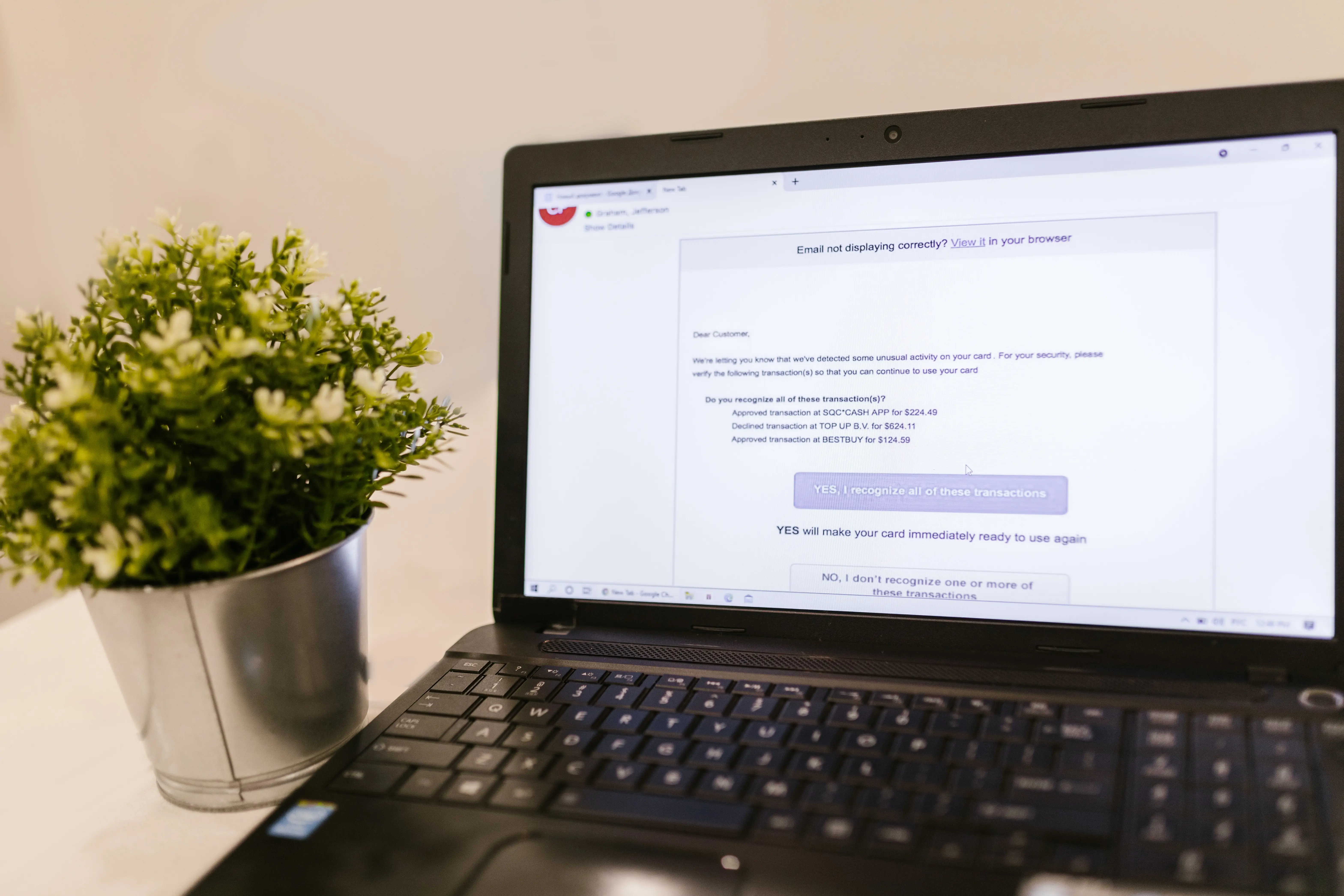
Email phishing continues to rise with the digitization and growth of e-commerce. Phishing has a huge impact on organizations where the main targets are financial departments (Naaz, 2021). It is an online social crime where attackers send malicious but unsuspecting email messages to trick people into falling for their predetermined scam. The emails intend to make the attacked conceal some vital information about their organizations that are later used for financial frauds and institutional conflicts departments (Naaz, 2021). Email phishing is a major issue in business and is considered an unethical practice that has arisen in the commercial industry. It is a threat to management and finance, and institutional security as most entities believe that their privacy is not sustained under such vulnerability. There is a greater need to address the situation to beef the belief in e-commerce and to ensure that the commercial sector is free of such a practice that dents its ethical codes. The essay describes the process of analyzing the dilemmas associated with email phishing using ethical principles of the slippery slope and the collective utilitarian.
The Use of Slippery Slope Principle in the Process of Analyzing Email Phishing Dilemmas
Email phishing contributes to some ethical questions on responsibility, trust, awareness, and self-control. As an ethical issue, the practice raises dilemmas because of the compromised ethical principles. Handling and controlling it throw the organization into controversies that are difficult to manage hence the dilemma. The analysis process of any ethical behavior is done in five steps that include identifying the issue, outlining the options, construction of ethical arguments, evaluation of the arguments, and making a decision. Email phishing has been singled out as an ethical trend in e-commerce (AbuRaya, 2020). It is important to list its moral and ethical implications in the first stage before considering options that can be adapted to respond to it in the next level. The third step is the construction of ethical arguments that match the practice in the discussion by determining moral principles and standards that best describe the situation. At stage four, it is important to weigh the arguments and determine how effective they are towards addressing the ethical issue raised before moving to step five where an individual and entity are expected to make decisions that would be sustainable and in line with the problem.
The concept of an ethical slippery slope defines behavior when a decision-maker first decides to deceive others by covering up past behavior. In email phishing, the attackers cover their intentions by sending enticing links through messages which unsuspecting employees click thereby subjecting their organization to planned hacking. Once the practice is initiated, it slowly sinks and becomes difficult to reverse as is the case today in the business. Privacy and confidentiality of financial records and information of many organizations have been threatened due to the practice that emerged from a single individual and became a wide practice that is hard to tame today. Email phishing has finally grown into media corruption in the business sector but from a simple practice (Wang et al., 2018). The desire to protect both consumers and businesses has led initiatives through analysis of the ethical dilemmas to protect them from cybercriminals who take advantage of unawareness of the situation (Chawla & Kumar, 2021). As a result, the five steps of dilemma analysis have been embraced throughout the slippery slope principle to identify the challenges raised by email phishing and to help tame them before many unsuspecting persons become casualties.
Email attackers are determined and committed to realizing their reasons for conducting the hacking process and if not quickly detected, their influence spreads. When good people conspire with those committing the offense through silence and ignorance, it becomes a new normal in the work atmosphere that contravenes ethical provisions. Notably, software corruption that contributes to email phishing when not reported or detected earlier enough slowly erodes e-commerce reputation and renders the attackers immoral while the targeted institutions are irresponsible and unaware of their security threats (Burr et al., 2018). Since any organization can become a casualty of the slippery lapses, every institution should consider the five steps in the dilemma analysis as they take proactive roles in curbing the challenge. Consequently, to avoid being thrown into the dilemmas of irresponsibility, trust, and unawareness, enterprises should develop mechanisms that protect their institutions from slow and steady downfall. Organizational leadership should focus on their roles that might have contributed to the phishing as they try to find solutions instead of pointing fingers at individual employees who might have been directly involved in the phishing.
The Use of Collective Utilitarian Principle in the Process of Analyzing Email Phishing Ethical Dilemmas
The principle of collective utilitarianism determines the usefulness of a process and activity depending on the pleasure that is obtained from it. Email phishing negatively impacts organizations on the receiving end while it benefits those who direct the attack. However, devoid of the direction of the attack, the whole idea of the act is unethical and should not be advocated. The dilemmas associated with phishing from the principle of utilitarianism are similar to those in the slippery slope since they affect the organization in the same magnitude. Email phishing has neither truth nor loyalty or justice versus mercy to the affected entities (Wang et al. 2018). Additionally, it is only good for the attackers but not the whole industry that relies on e-commerce. Also, email phishing has short-term goods to those involved before their practice is disclosed. Therefore, email phishing does not have overall happiness that can make it meet the demands of the principle of collective utilitarianism. The dilemmas associated with it are all short-lived on the side of attackers while they have negative effects on the sides of the impacted businesses.
In determining the effect of email phishing based on the utilitarian principle, it would be essential to raise moral questions touching the moral implications on both the targeted firms and those practicing it before developing actions and policies to be followed in responding to it. The questions would provide directions as to whether it is a good practice worth entrenching or a bad one to culminate. The next step in the analysis is the introduction of this principle of utilitarianism and the identification of possible basic ethical standards that the practice might have contravened. When the ethical standards converge, it would be advisable to determine the impacts of email phishing (Naaz, 2021). Illustratively, in this case, all the principles agree that email phishing is a negative trend that should be stopped and this position is supported by the ethical dilemmas surrounding it (Wang et al. 2018). The fourth stage incorporates evaluation of arguments derived from ethical dilemmas which will be crucial in making decisions about email phishing. When the results from the evaluation show and prove that the practice is unethical by contributing to immoral standards, the decision can be made in unison declaring it unsuitable and worth stopping for the success of e-commerce.
References
AbuRaya, R. (2020, November). Business Analytics of E-Commerce Policy and Practice: An Ethical Perspective. In 2020 International Conference on Decision Aid Sciences and Application (DASA) (pp. 761-767). IEEE.
Burr, C., Cristianini, N., & Ladyman, J. (2018). An analysis of the interaction between intelligent software agents and human users. Minds and Machines, 28(4), 735-774.
Chawla, N., & Kumar, B. (2021). E-commerce and consumer protection in India: The emerging trend. Journal of Business Ethics, 1-24.
Naaz, S. (2021). Detection of Phishing in the Internet of Things Using Machine Learning Approach. International Journal of Digital Crime and Forensics (IJDCF), 13(2), 1-15.
Wang, P., Cho, L. F., & Li, R. (2018). An institutional explanation of media corruption in China. Journal of Contemporary China, 27(113), 748-762.